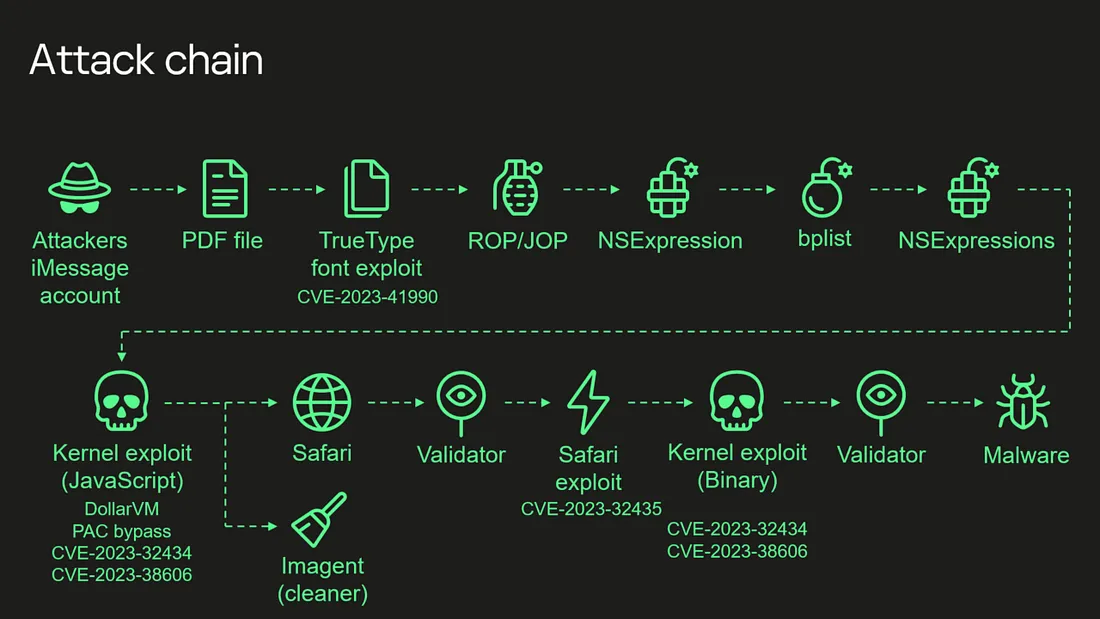
Backdooring iPhones using possibly the most advanced exploit ever
Read MoreProjects
Mind blowing projects
Frequently Asked Questions
Primarily focus on tech-driven solutions related to public infrastructure, cybersecurity, digital rights, and automation. Most of my projects aim to solve real-world problems using open data, APIs, and scalable web technologies.
Many of them are, yes. Whenever possible, I release code, documentation, or datasets under open licenses so others can learn from, build upon, or improve the work.
You can contribute in several ways:
Submitting pull requests or suggestions (if code is public).
Reporting bugs or sharing feedback.
Collaborating on research or technical writing.
Reaching out for joint initiatives or ideas.
Absolutely. I’m always open to new ideas, especially if they’re aligned with social impact, technology, and open innovation. Just drop me a message through the contact form or email.
I occasionally publish research papers, technical blogs, and experiments on this site and GitHub. Kindly check the navigation menu.
User Feedback




Read my Latest blog post
Cyber Threats, Hoaxes & the War of Misinformation: Dissecting the “Dance of the Hillary” and the India-Pakistan Digital Conflict
Uncover how the ‘Dance of the Hillary’ malware hoax spread across India, tricked law enforcement, and what it reveals about cybersecurity and disinformation warfare.
Read MoreFrom the First Flag to the First Footprint: The Journey of Hackorn
What started as a small CTF team in a university classroom in Greater Noida has now grown into a nationwide movement. Hackorn – The Berserk isn’t just about hacking competitions; it’s about building ethical warriors, teaching life skills, and giving back to society. From ranking in CTFs to running roadside Rasna drives, discover how one team is redefining cybersecurity education in India—and how you can be a part of it.
Read Moresing up to newsletter
receice latest news, updates, and many other things every week.