Introduction: A War Beyond Borders — Welcome to the Cyber Battlefield
As geopolitical tensions simmer between India and Pakistan, a parallel front has opened online — a space where keyboard warriors, hacktivist groups, and misinformation peddlers clash in a battle for perception, fear, and influence.
In this evolving landscape of cyber warfare, the real threat isn’t always malware—sometimes, it’s mass confusion. And at the heart of this digital drama lies one particularly viral hoax: “Dance of the Hillary” — a supposed Pakistani malware that never actually existed.
This guide unpacks the layers of technical disinformation, explores how threat actors weaponize social media, and explains how agencies and citizens can protect themselves from both actual cyberattacks and digital fearmongering.
Malware or Misinformation? Inside the “Dance of the Hillary” Hoax
The chaos began with a typical WhatsApp forward, warning of a highly dangerous malware named Dance of the Hillary, allegedly spread via Facebook, WhatsApp, and email. According to the message, it could steal passwords, compromise bank accounts, and even provide remote access to devices.
Even official LEA (Law Enforcement Agencies) handles echoed the claims, mistakenly amplifying the false alarm.
🔍 But here’s the technical truth:
Cybersecurity researchers, including Harsh Verma, confirmed that “Dance of the Hillary” is a recycled hoax—dating back as far as 2011 and re-emerging periodically, much like classic malware myths.
The warning included a reference to tasksche.exe, a legitimate Windows Task Scheduler binary, which cannot even run on Android or iOS devices — immediately discrediting the claim.
Role of Social Media and LEA Misinformation
One alarming trend is how official and unofficial digital handles—even some operated by LEAs—spread these hoaxes unintentionally.
CloudSEK and ThreatOSINT have reported hundreds of Pakistani-linked X (formerly Twitter) accounts pushing false narratives, including fake data leaks from the Ministry of Defence, PMO, and Election Commission of India.
Case in point:
A group named SYLHET GANG-SG claimed a breach of 247 GB from the National Informatics Centre (NIC). However, forensic analysis showed it was merely 1.5 GB of publicly accessible promotional files.
Real Cyber Threats Are Subtle – Meet APT36
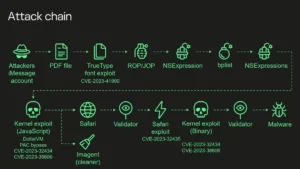
While public attention is often hijacked by hoaxes, Advanced Persistent Threat (APT) groups like APT36 (aka Transparent Tribe) are engaged in stealthy cyber operations targeting Indian military, intelligence, and government systems.
Key threat vector: Crimson RAT, a known Remote Access Trojan that facilitates full device compromise — from keystroke logging to webcam spying.
📌 In April 2025, APT36 leveraged the Pahalgam terror attack to initiate phishing campaigns directed at Indian personnel using fake emails mimicking MoD alerts.
🔗 Related Resource: Learn more on ThreatOSINT – India’s open-source investigation toolkit to analyze such cyber threats.
How to Identify a Fake Cyber Alert
Use this checklist to separate actual cyber threats from WhatsApp urban legends:
- Verified source: Check on websites like VirusTotal, ThreatKill, or PIB Fact Check.
- “Forwarded many times” label: Classic hoax sign.
- Lack of technical breakdown: No IOC (Indicators of Compromise), no CVEs.
- Poor grammar: Hallmark of fear-based phishing.
- Calls to “forward to others”: Common in chain scams.
🧠 Legit malware like Pegasus, Crimson RAT, or DarkHotel are thoroughly documented in MITRE ATT&CK and global threat reports.
ThreatKill & ThreatOSINT – Your Tools Against Misinformation
To help citizens and investigators alike, we’ve launched ThreatKill – a portal of official grievance links, cybercrime complaint portals, and reporting tools. Also explore ThreatOSINT – a curated database of cyber investigation tools including:
- Email Header Analyzers
- Social Media Dorking tools
- Fake Profile Generators
- Leaked Database Search
- Phone Number OSINT
- Public WiFi Sniffers
These tools aid in OSINT (Open Source Intelligence) gathering for ethical investigations and awareness.
Final Thoughts: Don’t Just Secure Your Devices—Secure Your Mind
The “Dance of the Hillary” hoax highlights how digital misinformation can go viral faster than actual malware — damaging trust and spreading panic.
In this era of disinformation warfare, our first line of defence is not software — it’s critical thinking.
🧠 “The only device this malware targets is your psychology.”
– Harsh Verma